Hacking group LulzSec trying to ‘incite cyber riot’
Hackers at LulzSec deny targeting the UK census as a suspected member of the group is questioned by police. But a security expert tells Channel 4 News they may be inciting “cyber riot”.
Police are questioning a 19-year-old man suspected of being a “major player” in LulzSec, a mystery group of international hackers which claims to have exposed security weaknesses at several major organisations in the UK and US.
A man named as Ryan Cleary, from Wickford in Essex, was arrested following a swoop by Scotland Yard and America’s FBI in a “pre-planned intelligence-led operation”.
The Metropolitam Police said in a statement that a “significant amount of material” had been seized.
But the LulzSec group has denied Ryan Cleary is their leader. A message appeared on the @LulzSec Twitter account which read “Seems the glorious leader of LulzSec got arrested, it’s all over now… wait… we’re all still here!”
An apparent hack on computers at the UK 2011 Census has also been denied with the group saying “that wasn’t us”. A spokesperson from the census said they are “working with security advisers” but there was “no evidence” so far of a breach.
Earlier this year stolen data from security fobs was used to break into computers at US arms firm Lockheed Martin.
More from Channel 4 News: Hacked security giant offers to replace 40m key fobs
Lockheed’s data handling department coordinated the UK census after being awarded the contract by the Office for National Statistics (ONS).

‘Cyber riot’
A cyber-threat expert at a major UK financial institution has spoken to Channel 4 News about what he sees as a “step change” in activity by LulzSec.
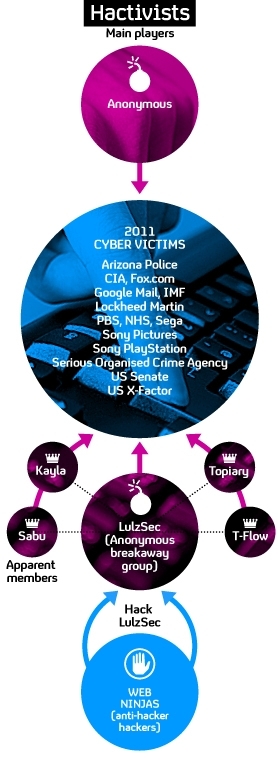
Authorities in Britain and the US have been trying to trace the group for several weeks following apparent attacks on the CIA, the US Senate, Nintendo, Sony, the X-Factor and US television networks PBS and Fox. In the UK the group has also claimed to have found security flaws in systems at the NHS.
This kind of threat is definitely here to stay and whilst arrests will have an impact on LulzSec, hacktivism is here to stay. Cyber-threat officer
The intelligence officer, who works to protect his organisation and wished to remain anonymous, said: “Their aim is to expose ‘laughable’ security at big organisations. They are quite simple cyber attacks.
“But they appear to have got bored and moved on.
“They went from targeting individual organisations to large initiatives – under the banner of the #AntiSec operation.
“That is a step change… it seems like the buzz [of the first alleged breaches] had worn off and they have thought ‘can we incite a cyber-riot?'”
He added: “This kind of threat is definitely here to stay and whilst arrests will have an impact on LulzSec, hacktivism is here to stay.”
Rival hackers
Two days before the FBI and officers from the Metropolitan Police made the arrest, a separate group of hackers claimed it had uncovered the identities of LulzSec members and handed the information to authorities.
The group, calling itself “web ninjas” said that it had exposed personal information about LulzSec to help victims of hacking.
On Sunday, the group posted online: “Due to the sensitivity of information, we are directly sending the information to FBI now but still will publish some info on the BLOG.”
LulzSec appears to deny that any of its members, believed to be six people, have been arrested.
And “web ninjas” appeared to corroborate LulzSec’s denial that its “leader” had been caught.
A hacker affiliated with the former said that it was common knowledge that a 34-year-old hacker using the alias “Sabu” was its chief. The group said that the ringleader’s name, address and location had been handed over to the FBI.
Another hacktivist group, Anonymous, has also distanced itself from Ryan Cleary.
The arrest in Essex comes 10 days after police in Spain police arrested three alleged members of Anonymous for allegedly taking part in online attacks against Sony’s PlayStation network, as well as other infiltrations of banks, businesses and government websites.
It also seized a server used in the attacks from the home of one of the suspects.
-
Latest news
-
‘Authentic Stupidity’: Ben Elton’s new show explores how idiotic human beings can be5m

-
Is Israel’s evacuation of Rafah the precursor to full scale invasion?3m

-
Eurovision: Non-binary artist wins for first time2m

-
Tens of thousands march in Georgian capital against ‘foreign agents’ bill2m

-
‘Russia’s number one goal is to get troops closer to Kharkiv,’ says Ukrainian security analyst4m

-




